A technical code fragment has been discovered on the New York Times website, revealing backend security and tracking mechanisms used by the publication. The code snippet contains various technical parameters including runtime configurations, client identification numbers, hash values, and security tokens. The fragment shows a variable declaration with multiple data points: a runtime type marked as 'c', a client ID string 'AHrlqAAAAAMAvAEsEb9w-s8AeVgFqA', and a hash value '499AE34129FA4E4FABC31582C3075D'. The code also includes a session size parameter of 17,439 bytes and references to geo-location captcha delivery systems hosted at 'geo.captcha-delivery.com'. Additionally, the fragment contains an encrypted security token and cookie data used for user session management and authentication purposes. This type of code is typically used by major news websites to manage user interactions, prevent automated access, and ensure secure content delivery. The presence of such technical elements highlights the complex infrastructure required to operate a major digital news platform like the New York Times, where security measures and user tracking systems work together to maintain site functionality and protect against unauthorized access.
Latest article
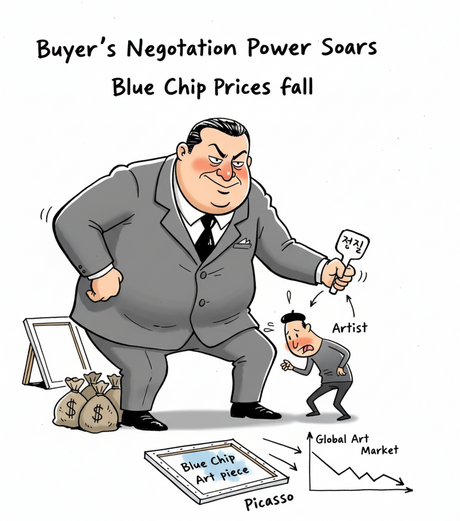
- Frozen Politics, Frozen Art: Hoping for a Thaw in Korea’s Art Market Next Year
- Boom or Mirage? National Museum of Korea Debates Paid Admission Amid K-Culture Surge
- Billboard Names K-Pop as a Defining Force in 2025 Pop Culture
- Diagnosing the Global Art Market in 2025: Between Correction and Reconfiguration
- Korea Sets New Tourism Record as Inbound Visitors Hit 18.5 Million in 2025
- NFM Releases Landmark Report on Village Beliefs Across Gangwon: Which Spirits Protected These Mountain and Coastal Communities?
- Online Poster Comparing Cho Jin-woong to National Heroes Sparks Backlash
- Why Lee Byung-hun Deserves to Win the Golden Globe