A technical security system has been activated on a website, displaying code-related information that appears to be part of an automated security verification process. The system generated various technical parameters including routing identifiers, session tokens, and host verification data. This type of activation typically occurs when websites implement security measures to protect against automated traffic or potential security threats. The displayed information includes encrypted hash values, client identification numbers, and cookie authentication data that are commonly used in web security protocols. Such security implementations have become increasingly common as websites work to maintain safe browsing environments for their users while preventing unauthorized automated access attempts.
Latest article
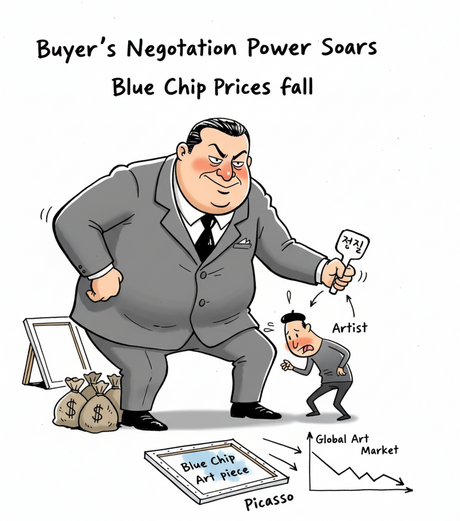
- Frozen Politics, Frozen Art: Hoping for a Thaw in Korea’s Art Market Next Year
- Boom or Mirage? National Museum of Korea Debates Paid Admission Amid K-Culture Surge
- Billboard Names K-Pop as a Defining Force in 2025 Pop Culture
- Diagnosing the Global Art Market in 2025: Between Correction and Reconfiguration
- Korea Sets New Tourism Record as Inbound Visitors Hit 18.5 Million in 2025
- NFM Releases Landmark Report on Village Beliefs Across Gangwon: Which Spirits Protected These Mountain and Coastal Communities?
- Online Poster Comparing Cho Jin-woong to National Heroes Sparks Backlash
- Why Lee Byung-hun Deserves to Win the Golden Globe